RSA SecurID Two-factor Authentication System
RSA SecurIDTwo-factor Identity Authentication System
RSAprovides a complete solution
among the five functions of network information security (identity authentication, authorization, confidentiality, integrity and non-repudiation), identity authentication (Authentication) is the most basic and important link, even if authorization, confidentiality, integrity, and non-repudiation are The links are well done, but if the legal account and password are embezzled to log in to the system, the system still considers him a legal user and gives him corresponding access rights, put the system in a dangerous state.
RSAprovides a complete identity authentication solution, especially RSA SecurID two-factor identity authentication solution, which has become the de facto standard in this field. The solution has won wide trust in the field of information security with its easy implementation, maturity and reliability.
RSA SecurID: Powerful two-factor authentication system
simply put, two-factor authentication is an authentication system that works only by combining what you know and what you can have. For example, a bank card withdrawing money from an ATM is an example of a two-factor authentication mechanism that requires a combination of the withdrawal password and the bank card.
RSA SecurIDis a powerful identity authentication system. The usage is that the administrator issues a separate authentication device (which can be analogous to a bank card, which we usually call a token) to authorized users. This authentication device generates a unique unpredictable token every minute according to time changes. Code. When the user uses this authentication device for the first time, he needs to set his own personal code (we call it a PIN code, which can be compared to the withdrawal password of a bank card). When in use, the user's personal code is combined with the token code to form a two-factor authentication code (we call it passcode to distinguish the password of static passwords);RSA's time synchronization authentication technology will ensure that the token and the authentication server generate the same token code at the same time, so that only legal users holding the token can access the resources they can access.
Among the commonly used network security technologies, identity authentication technology is the foundation of other security technologies. By combining with other technologies, it can provide a more secure and suitable solution for application.
According to IDC's authoritative statistics, RSA has gained more than 70% market share in the global identity authentication market and has become the de facto standard for identity authentication. At the same time, RSA is SecurID supported by more than 370 products worldwide, which can well protect users' investment.
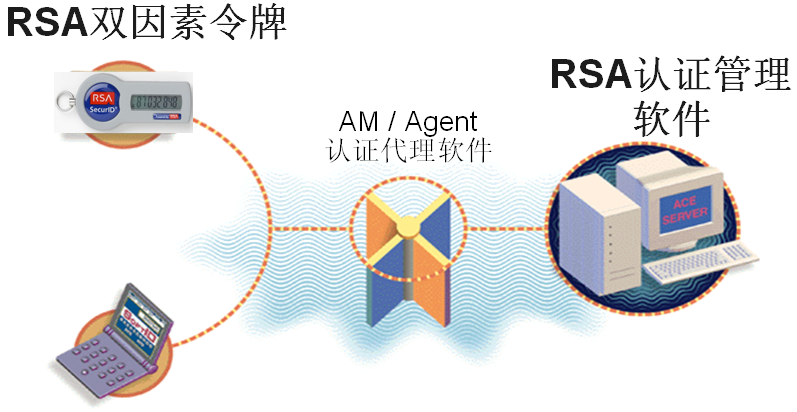
RSA SecurIDTwo-factor authentication system components
RSA SeucrIDconsists of authentication server RSA Authentication Manager (AM), agent software RSA Authentication/Agent, authentication equipment and authentication application programming interface (API) (as shown in the following figure).
certificationmanagement software (Authentication Manager)
RSA Authentication Manager (certification management) software is a certification management system that combines a certification engine with excellent performance and centralized management functions. Taking authentication as an example, when the authentication server (the server that installs the authentication management software) receives an authentication request, it uses the same algorithm and seed value as the user authentication device (token) to verify the correct token code. If the user enters the correct token code, the authentication passes, and the user can access the resources to which he has access.
RSA SecurIDtwo-factorauthentication equipment
When we talk about authentication devices, we usually refer to two-factor authentication tokens. There are many types of tokens. Take RSA 700 hardware tokens as an example. The chip and battery have been built into the token, and the RSA algorithm has been solidified in the chip. This algorithm is related to the time factor. Each token has a unique 128-bit seed file. The seed file combines a specific time synchronization algorithm to generate a dynamic token code every 60 seconds. Each token is issued to a different user, and the user is required to set a PIN code when using the token for the first time. Later, every time the user of this token uses the token to access the resources he wants to access, he needs to enter the PIN code and the combination of the token at the same time. This is what we call the passcode, that is, the two-factor password.
After receiving the authentication request from the authentication agent software, the authentication server only needs to compare whether the token code entered by the user of the token is consistent with the token code generated by the authentication server to determine whether the user is a legitimate user.
can be seen, RSA strong authentication system is based on the same time, the same algorithm, the same seed file generated by the same operation result (token code) such a simple but extremely effective way to achieve identity authentication. Therefore, there is no need for any communication between the token and the authentication server, and its core lies in RSA's time synchronization patented technology.
RSA 700Two-factor Token
RSA two-factor software and hardware tokens. The following is a brief introduction to 700 hardware:

the size of the token is as good as an ordinary key (approximately5.8cm long,23cm wide and nearly thick1cm). The token is already built-in128-bit seed file has been initialized to facilitate direct use by customers. Each token has a unique serial number that identifies each piece of token. Unique for each token128-bit seed file is stored on a seed CD when the token is ordered, so that the seed file can be imported into the authentication server.700type hardware tokens are6bit sum8digits are the same.